When the White House disclosed that senior US officials were using the free messaging app Signal for a private group chat, it made headlines.
Jeffrey Goldberg, the chief editor of the Atlantic, was among the group that inadvertently discussed plans for an attack against the Houthi group in Yemen.
There has been a massive backlash after Democratic Senate leader Chuck Schumer called it “one of the most stunning” military intelligence leaks in history and called for an investigation.
However, what is Signal in reality, and how safe were the communications between the top politicians on it?
The app for security

Joe Tidy, a cyber correspondent, describes the operation of end-to-end encryption.
With an estimated 40–70 million monthly users, the security app Signal is relatively tiny in comparison to the two most extensive messaging services, WhatsApp and Messenger, which have billions of users. However, security is one area where it does set the standard. End-to-end encryption (E2EE) is at the heart of that.
In short, it means that Signal itself cannot read messages; only the sender and the recipient can. Additionally, these features don’t need to be diluted to increase revenue: The Signal Foundation, a US-based non-profit that depends on donations rather than ad revenue, owns Signal.
Following the release of the US national security story, Meredith Whittaker, the company’s boss, wrote on X that “Signal is the gold standard in private comms.” Signal’s “gold standard claim” is what attracts journalists and cybersecurity specialists, who frequently use the app.
However, even that level of security is considered insufficient for high-level discussions about extremely sensitive national security issues. This is because using a mobile phone to communicate carries an essentially inevitable risk: the device’s security depends on the user.
Your messages will be visible to anyone who manages to access your phone while Signal is open or who figures out your password. Furthermore, if you are using your phone in a public place, no app can stop someone from looking over your shoulder.
High-ranking security officials using a messaging app like Signal to communicate is “very, very unusual,” according to data expert Caro Robson, who has experience working with the US government.
“Normally, you would use a highly secure government system that is owned and operated by the government, utilizing very high levels of encryption,” she explained.
According to her, this usually refers to gadgets stored in “extremely secure government-controlled locations.”
Historically, the US government has discussed national security issues in a sensitive compartmented information facility, known as SCIF, which is pronounced “skiff. Personal electronic devices are not permitted in a Scif, which is a highly secure enclosed space.
According to Ms. Robson, “you have to be in a specific room or building that is constantly swept for bugs or any listening devices even to access this kind of classified information.” Scifs can be found in a variety of locations, including official residences and military bases.
“The government’s own highest standards of cryptography are used to secure and encrypt the entire system,” she stated. “Especially when defense is involved.”
Records and encryption
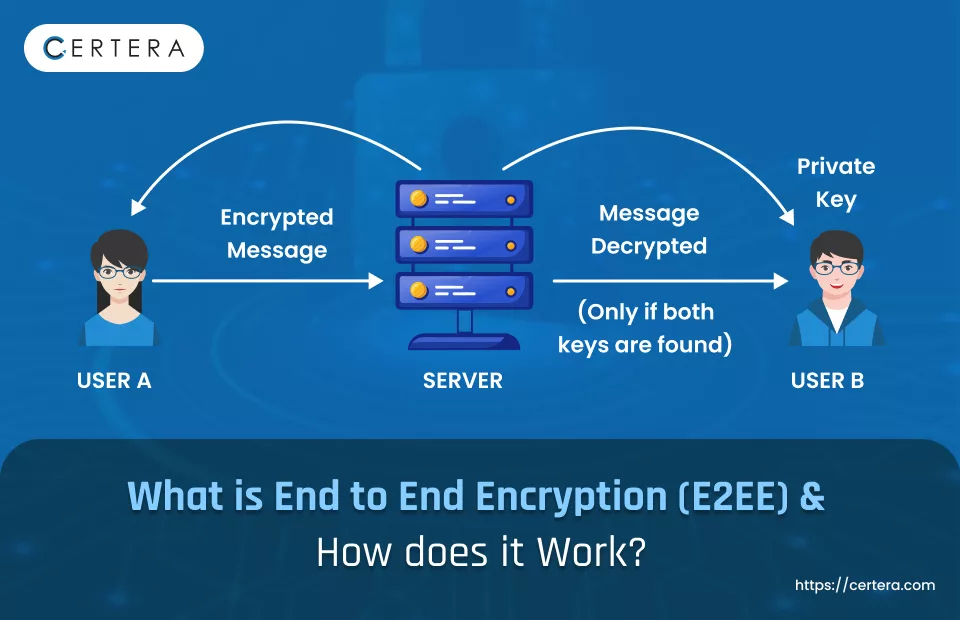
End-to-End Encryption and How It Works.
Disappearing messages are another Signal-related problem that has sparked worries. Like many other messaging apps, Signal lets users configure messages to expire after a predetermined amount of time. According to Jeffrey Goldberg of The Atlantic, after a week, some of the messages in the Signal group he was added to vanished.
Unless users of the app forward their messages to an official government account, this might be against record-keeping laws. Additionally, this is far from the first row that involves E2EE. To read messages they believe could pose a national security risk, several administrations have sought to establish a so-called backdoor into messaging services that utilize it.
Apps like WhatsApp and Signal have previously opposed efforts to open such a backdoor, claiming that malicious actors would eventually use it. If lawmakers weakened the app, Signal threatened to remove it from the UK in 2023.
Apple, which also uses E2EE to protect specific files in cloud storage, got into a major dispute with the UK government this year. After the government demanded access to data that Apple had protected in this way, the tech giant decided to remove the feature entirely in the UK. The case is still pending.
However, as this controversy demonstrates, if you give your private information to the wrong person, it doesn’t matter how secure or protected you are by the law.
Or, to put it more bluntly, “Encryption can’t protect you from stupid.”




